Dynamics 365 Business Central 2023 Wave 2 release (version 23) and the new AL language version 12 introdocues a new data type called SecretText. This new data type can be used to protect secrets in AL code from being revealed through debugging.
SecretText data type will be usable as a:
- Variable value
- Return value
- Parameter value
The SecretText type encapsulates a Text type. If a Code or other text type is to be stored, it’ll be converted into the Text type.
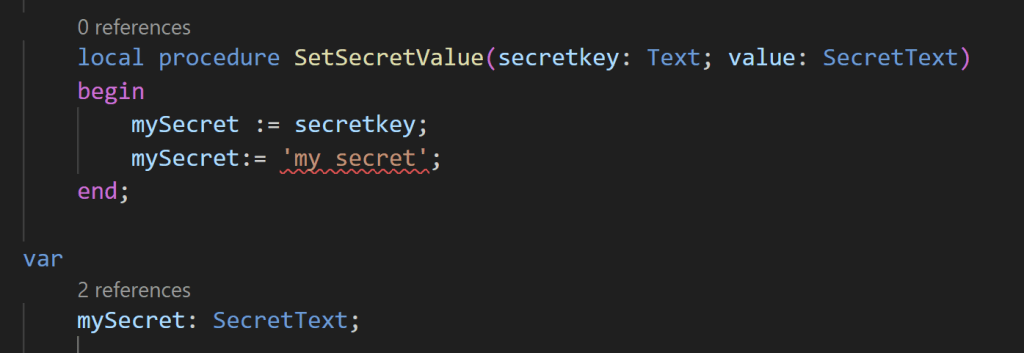
You can assing to a SecretText variable a Text variable but you cannot implicitly convert a Text type to a SecretText:
At the time of writing this post its usage is quite limited to handlig secrets in AL code and doing Http calls with HttpClient.
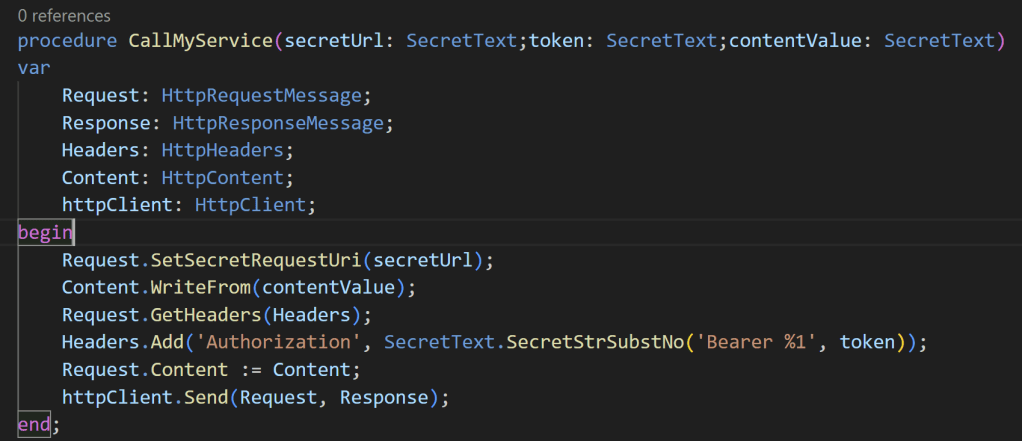
An example of usage of the new SecretText data type with HttpClient is the following:
As you can see from the above example, now the HttpRequestMessage, the HttpContent and the HttpHeaders objects support adding a SecretText value to their methods for composing an Http call.
SecretText is not supported everywhere at the time of writing this post. For example, IsolatedStorage methods for setting a key at the moment does not supports it (but in the future this should be possible):

A SecretText data type supports the UnWrap method that returns the contained text inside the SecretText object as a plain text value:
procedure Unwrap(): Text
This method exists for compatibility reasons and its use is discouraged as it can lead to secret exposure.
Is also supports the IsEmpty method that returns a value indicating whether the secret text contains any content:
procedure IsEmpty(): Boolean
Other important parts where at the moment the new SecretText data type is not supported are the Azure Functions and Blob Storage modules. Here is an example of a line of code for authenticating to an Azure Function via code authentication:
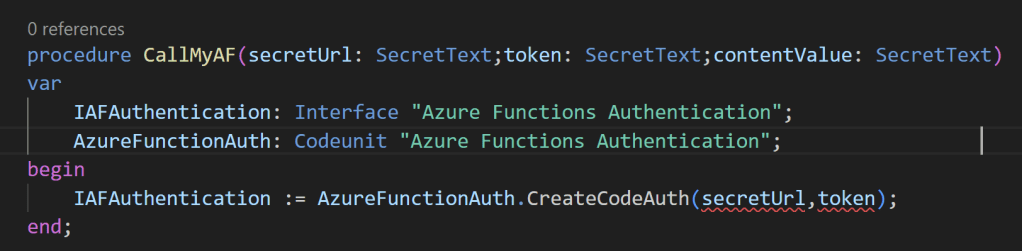
As you can see, the method only supports Text parameters at the moment.
Can you use SecretText data type now?
YES. You can start using this new data type in your extension code if you want to handle secrets in AL code and protect them from debugging (without marking methods as NonDebuggable). Not all standard modules and objects support it at the moment and these parts are probably where you will have to handle security of secrets in the old way. Bu things will change…